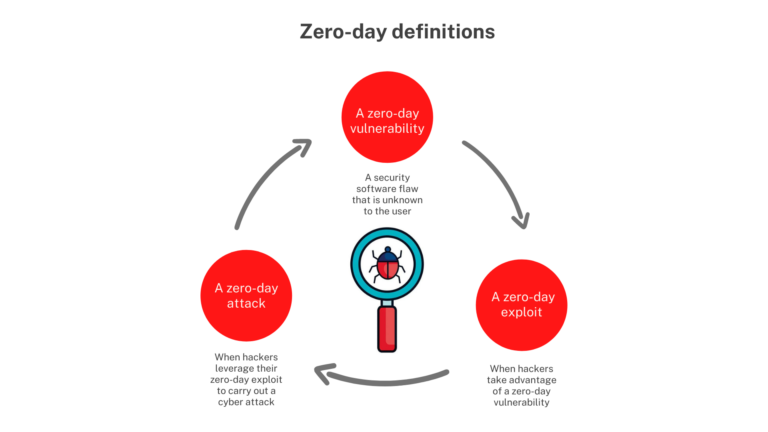
A zero day vulnerability is an exploit that happens before a software or hardware developer becomes aware of it. This gives the developer “zero days” to create a security patch and fix it.
Hackers can exploit these vulnerabilities to steal data, money, or cause damage. They often sell them on the dark web to other cybercriminals.
YBERSECURITY HEAT
Zero-day vulnerabilities are undiscovered flaws in software or hardware that hackers can use to breach systems and access sensitive data or critical systems. These attacks can lead to unauthorized access, financial fraud and loss of business continuity.
Threat actors employ sophisticated techniques that evade traditional security defenses including file inspections by Secure Web Gateways and anti-virus engines, sandboxing, network and HTTP inspections, malicious link analysis, offline domain analysis and indicator of compromise feeds. They rely on a combination of adaptive attack tactics such as HTML smuggling, email luring with hyperlinks and Excel 4.0 macros to get past these defenses.
The key to defending against zero-day attacks is real-time visibility of the attack surface combined with a micro-segmentation architecture. Using this approach, IT ops and security teams can detect new connectivity, anomalous behavior and changes in application performance that indicate an attack is underway.
Stuxnet
When Stuxnet appeared in 2010 and disrupted uranium centrifuges at Iran’s nuclear program, it became clear that we had entered a new era of cyber warfare. The worm was carefully designed to take over and modify specific models of industrial control systems, causing the equipment to malfunction while feeding false data to system monitors that everything was working properly.
The malware was complex, requiring multiple zero-day vulnerabilities, rootkits, stolen digital certificates, and more to infiltrate and spread. “It definitely took a team of professionals to create it,” said Kaspersky Lab’s Schouwenberg, who estimates the effort required two years.
Fortunately, regular computer users have little to worry about, as the zero-day vulnerabilities that Stuxnet exploited are now patched. Still, it’s important to practice good cyber hygiene and keep operating systems and security software up to date.
Sony Pictures Entertainment
On November 24, 2014, a group calling themselves Guardians of Peace broke into Sony’s computer systems and stole information. The hack resulted in embarrassing emails from executives, the complete copies of unreleased movies, and even personal data on 47,000 current and former employees.
The hackers also threatened theaters that were going to screen the film, The Interview, which was a satire of North Korea’s leader, Kim Jong-un. The threat resulted in a majority of the major movie chains pulling the film from their theaters.
The incident was a wake-up call for many companies. It showed that cybersecurity breaches can have a huge financial impact beyond reputational damage. This is why it is so important to protect your business from zero day vulnerabilities with a defense in depth security strategy like Heimdal’s.
Microsoft Skype
Skype (skIp) is a proprietary instant messaging, voice and video call application developed by Skype Technologies, which is owned by Microsoft. It is available for desktop computers, mobile phones and video game consoles. It allows users to make free calls and send messages to other Skype users. It also offers videoconferencing, file transfer and debit-based calling to landline and mobile telephones.
Due to its peer-to-peer architecture, Skype traffic is vulnerable to eavesdropping and monitoring by governments and other organizations such as the National Security Agency under the PRISM surveillance program. This is despite the fact that Skype incorporates features designed to thwart traffic analysis and obfuscate user identities. Administrators will need to be careful in applying the May Patch Tuesday releases. Six of the new CVEs were rated critical, including one in Microsoft’s Windows local security authority spoofing vulnerability that impacts Skype for Business and Lync and could allow remote code execution.
Apple iOS
The security updates Apple released on Friday for iOS, iPadOS, macOS Big Sur and macOS Monterey address two separate flaws that allow arbitrary code execution. Both were described as “actively exploited” in the wild by researchers Clement Lecigne and Donncha O Cearbhaill of Google TAG and Amnesty International’s Security Lab, respectively.
The first, tracked as CVE-2023-28206, is an IOSurfaceAccelerator out-of-bounds write vulnerability that can cause data corruption or device crash. The second, CVE-2023-28205, is a WebKit use after free weakness that can be triggered when a maliciously crafted web page processes a memory object.